Penetration Testing & IT Security Analysis
Optimize your company's IT security with our Penetration Testing & IT Security Analysis
Criminal hackers can exploit vulnerabilities in your network, your IT systems, applications or mobile devices to penetrate your organization and manipulate or steal sensitive business information and customer data. The fact of the matter is, no organization is "too small" or "too insignificant" for an attack, and many organizations are already compromised without even knowing it. Do you know the weak points in your systems and applications that attackers could exploit? Internal and external penetration tests and IT security analysis from TÜV Rheinland can provide those answers.
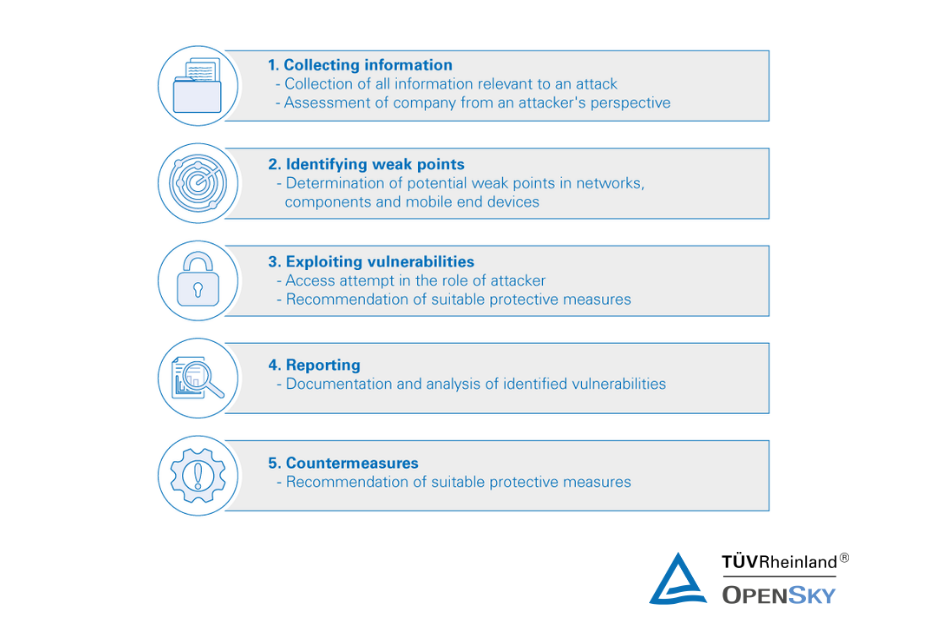
During our tests, we analyze your IT infrastructure and/or applications from the viewpoint of a hacker. In doing so, we simulate a realistic cyber attack and detect vulnerabilities in your IT before hackers can exploit them. After testing, our experts will inform you if and how your IT is vulnerable, the consequences they may bring for your organization, and offer recommended countermeasures to eliminate the detected vulnerabilities so that you can better protect your organization, your data, and your know-how in the future.
Scroll below to learn more about the procedure and benefits of Penetration Testing and IT Security Analyses from TÜV Rheinland!
During our tests, we analyze your IT infrastructure and/or applications from the viewpoint of a hacker. In doing so, we simulate a realistic cyber attack and detect vulnerabilities in your IT before hackers can exploit them. After testing, our experts will inform you if and how your IT is vulnerable, the consequences they may bring for your organization, and offer recommended countermeasures to eliminate the detected vulnerabilities so that you can better protect your organization, your data, and your know-how in the future.
Scroll below to learn more about the procedure and benefits of Penetration Testing and IT Security Analyses from TÜV Rheinland!







